Nanocore Malware Analysis
Date: Apr 24, 2025
TABLE OF CONTENT
1) Background 2) Static Analysis of the Sample: 3) Dynamic Analysis Of The Sample 4) Static Analysis Of cckgcf.exe 5) Dynamic Analysis Of cckgcf.exe 6) Static Analysis Of cckgcf-dump.exe 7) STATIC ANALYSIS OF RCDatalaststage.bin 8) Dynamic Analysis of Nanocore_Client.exe(rcdatalaststage.exe 9) Indicator Of Compromise:
Background
NanoCore RAT (Remote Access Trojan) is a type of malware designed to provide remote control over infected Windows systems. First emerging around 2013, it quickly gained popularity among cybercriminals due to its low cost and powerful features. It is often spread through phishing emails with malicious attachments and has been used in numerous cyberattacks worldwide. Its modular design also supports plugins, making it highly adaptable and dangerous, especially for unprotected systems.
**Our Sample For Today: Sha256:**1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511


Static Analysis of the Sample:
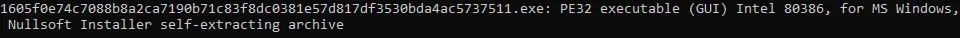
The output of the file command tells us that its a self-extracting archive We could extract the content in the file via 7-Zip or any other tool

Die(Detect It Easy) indicates that it is packed/compressed and a installer called Nullsoft Scriptable install System, a legitimate software to create windows installers
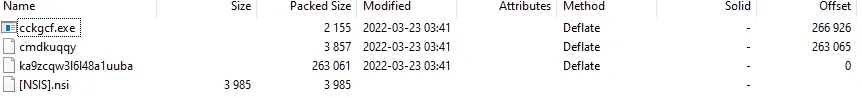
Present with 4 files,out of which 3 are crucial cckgcf.exe, cmdkuqqy, ka9zcqw316148a1uuba Some imports



Dynamic Analysis Of The Sample

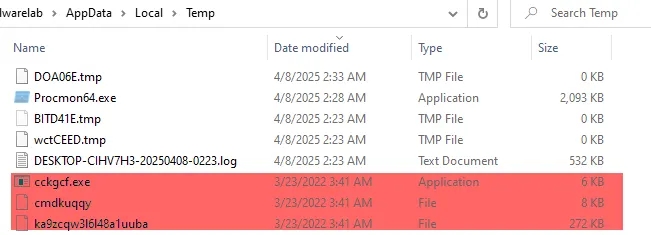
It Drops the files in C:\Users{0}\AppData\Local\Temp and Executes the cckgcf.exe with cmdkuqqy as its argument

It then cckgcf.exe again but with a different PEB address , Non-existent Parent Process and different file size Indicating Process Hollowing being used here.

Static Analysis Of cckgcf.exe
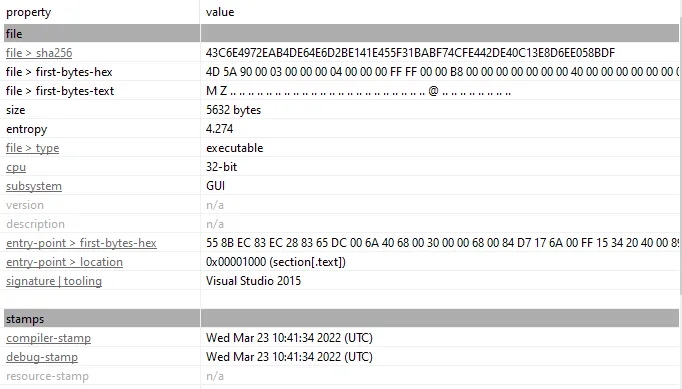

Suspicious Dll’s: MAPI32.dll — Used for email operations such as sending messages or accessing email data WININET.dll — Accessing The Internet MSWSOCK.dll — C2 Connection Via Socket CRYPT32.dll — Encryption,Decryption
Dynamic Analysis Of cckgcf.exe
Upon Initial Detonation Of cckgcf.exe With cmdkuqqy As Its Argument We Observed before
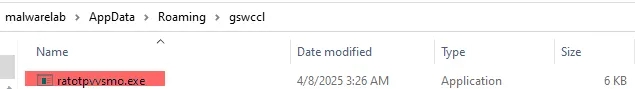
The Size of the file is the same as cckgcf.exe Upon analyzing both of them in DIE.exe we observed that its a copy oof cckgcf.exe
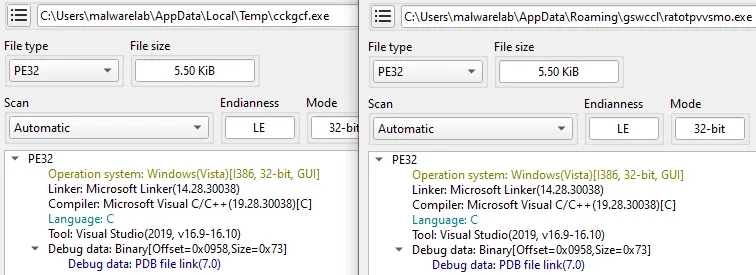
While Debugging the sample came across the following

It tries to virtually allocate Memory-If it fails then it jumps to the exit function which terminates the program
After That It retrieve the command line argument
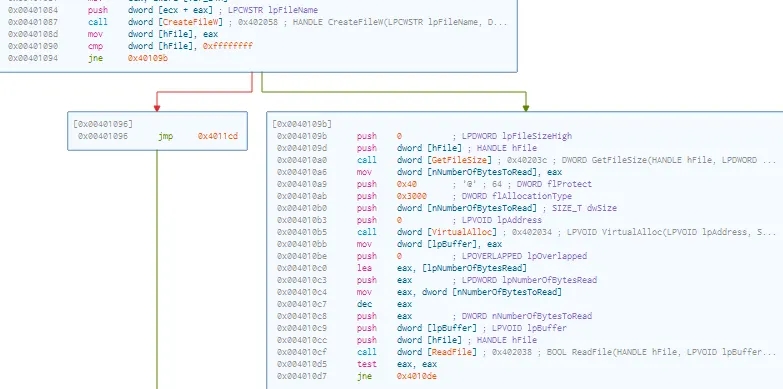
Then it uses CreateFileW to get a handle of it if it is unsuccessful it exists
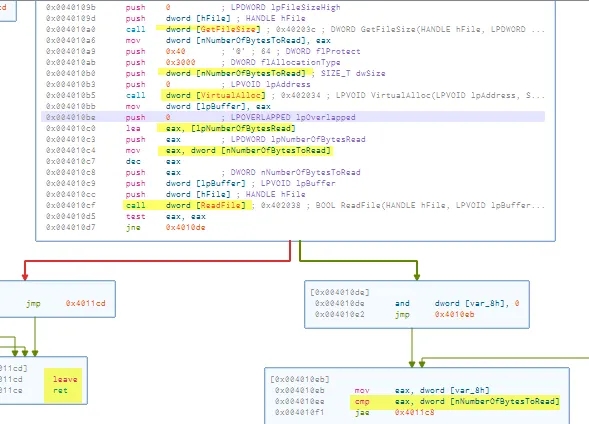
Then It Gets FileSize of it,then allocates memory,then reads the file if that’s unsuccessful then it exits, then moves to a big loop which does some kind of decryption then loads into eax then jumps into it

Loading the file’s x32dbg we see the following: I came across a lot of executable’s in while parsing through the executable
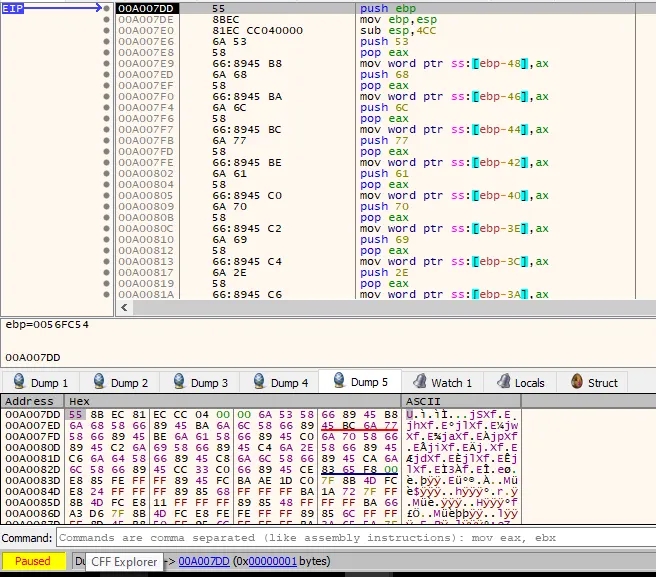
Here’s when the juicy part comes

After we jumped into the value in eax we were jumping again to a different memory location while parsing through the executable i placed a few breakpoints


Its Getting the temp path & appending the ka9zcqw316148a1uuba to it checking if it exists in the temp directory or not if it doesn’t exists then it just exits

Proceeds to get filesize ,allocates virtual memory upon tracking the memory region we found the below

Then it enters a loop where each time it iterates it deobfuscates one byte Final Deobfuscated Executable as follows
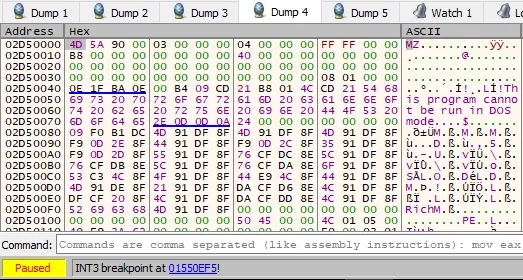
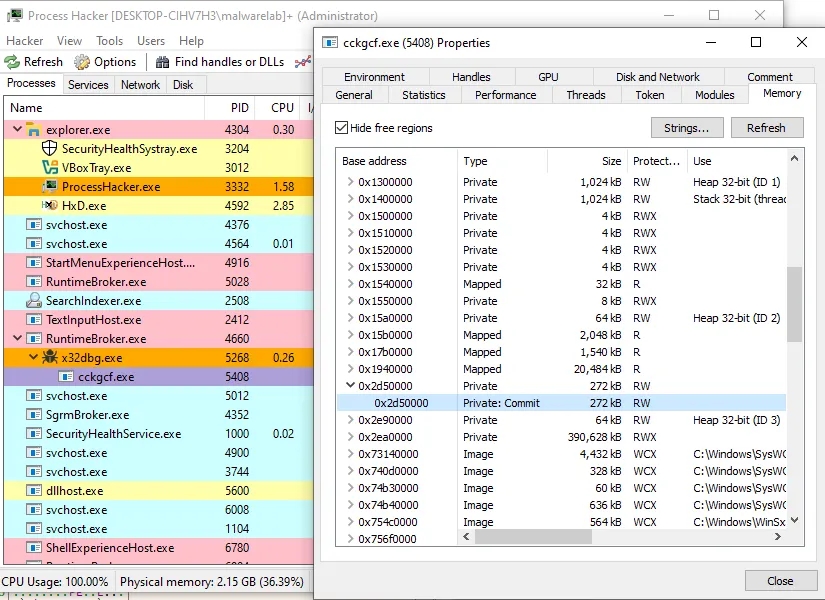
I dumped the memory region via processhacker

As far as i observed it used process hollowing and created another instance of itself with the deobfuscated executable
Static Analysis Of cckgcf-dump.exe

It indicates that its a .net executable and protected via Eazfuscator which is a commercial obfuscator For Deobfuscating i’ve used de4dot.exe you could use the following too EazFixer_. _Viewing the capabilities using Capa:
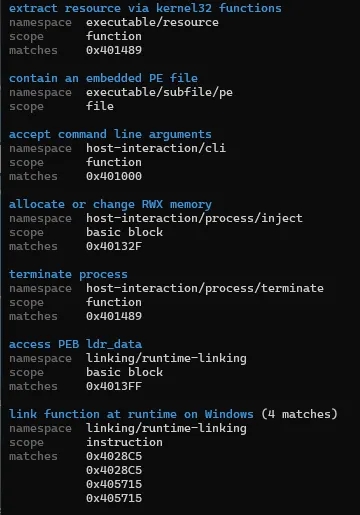

PeStudio later on detects a file inside the resources specifically in the rcdata section


Opening Resource Hacker as above and dumping the executable i’ve named it RCDatalaststage.bin
STATIC ANALYSIS OF RCDatalaststage.bin

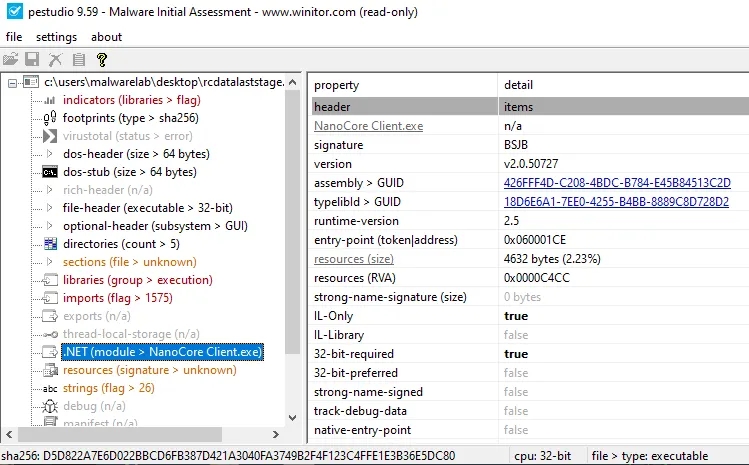

Analyzing Executable in dnSpy after Deobfuscating it with de4dot.exe
Heres Some Hard-Coded Data I found Possibly C2 Configuration
{ “BuildTime”, DateTime.UtcNow }, { “Version”, new Version(0, 0, 0, 0) }, { “Mutex”, Guid.Empty }, { “DefaultGroup”, “Default” }, { “PrimaryConnectionHost”, “127.0.0.1” }, { “BackupConnectionHost”, string.Empty }, { “ConnectionPort”, (ushort)9033 }, { “RunOnStartup”, false }, { “RequestElevation”, false }, { “BypassUserAccountControl”, false }, { “BypassUserAccountControlData”, null }, { “ClearZoneIdentifier”, true }, { “ClearAccessControl”, false }, { “SetCriticalProcess”, false }, { “PreventSystemSleep”, true }, { “ActivateAwayMode”, false }, { “EnableDebugMode”, false }, { “RunDelay”, 0 }, { “ConnectDelay”, 4000 }, { “RestartDelay”, 5000 }, { “TimeoutInterval”, 5000 }, { “KeepAliveTimeout”, 30000 }, { “MutexTimeout”, 2500 }, { “LanTimeout”, 2500 }, { “WanTimeout”, 8000 }, { “BufferSize”, 65535 }, { “MaxPacketSize”, 10485760 }, { “GCThreshold”, 10485760 }, { “UseCustomDnsServer”, false }, { “PrimaryDnsServer”, string.Empty }, { “BackupDnsServer”, string.Empty }, { “ShowInstallationDialog”, false }, { “InstallationDialogTitle”, string.Empty }, { “InstallationDialogMessage”, string.Empty }, { “InstallationDialogIcon”, (byte)0 }







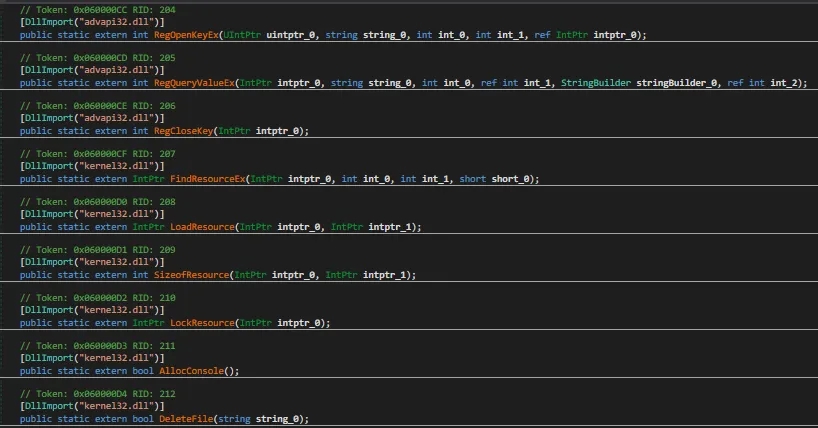
Dynamic Analysis of Nanocore_Client.exe(rcdatalaststage.exe

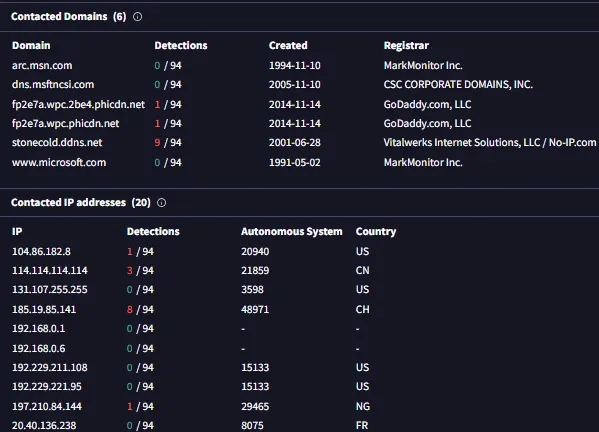
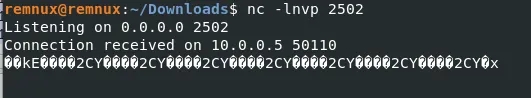
Its trying to reach stonecold.ddns.net As we saw earlier in virustotal it was flagged as malicious Its mostly a c2c server for the malware After Adding the domain in my /etc/hosts as localhost
Indicator Of Compromise:
Sha256:1605f0e74c7088b8a2ca7190b71c83f8dc0381e57d817df3530bda4ac5737511 MD5:6BD5C08C6084A3B3C2A527C6A31E6DE MD5:65AF831BAEE4AC0FCDB8EC7798767529 Domain :stonecold.ddns.net Port:2502 Ipv4:185.19.85.141
Linkedin:https://in.linkedin.com/in/nitin-mithbavkar-a65b7727a
Last updated